Don’t trade accessibility for security, or vice-versa
How do you secure access to sensitive resources while still making access reasonably easy for users who need it?
Risk-based authentication answers the question by making access easier or more difficult, depending on the risk an access attempt poses.
Context-based assessment
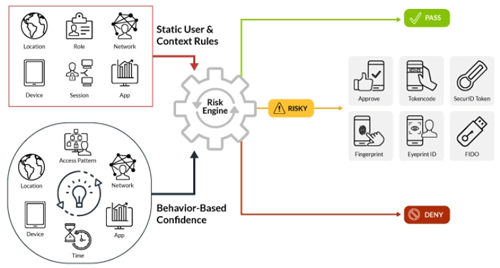
RSA risk-based authentication uses techniques and technologies—including data collection, device matching, anomaly detection, and behavioral analytics—to determine the context for an access attempt. It looks at who is requesting access, where they’re located, and what device they’re using. Based on the context, it then assesses the access risk.

Machine learning
In addition to assessing the risk access requests pose, RSA risk-based authentication learns from its assessments and applies that knowledge to future requests. For example, the same user requesting access to the same resource from the same device every day won’t be challenged. But if the same user requests access on a new device they will be challenged.
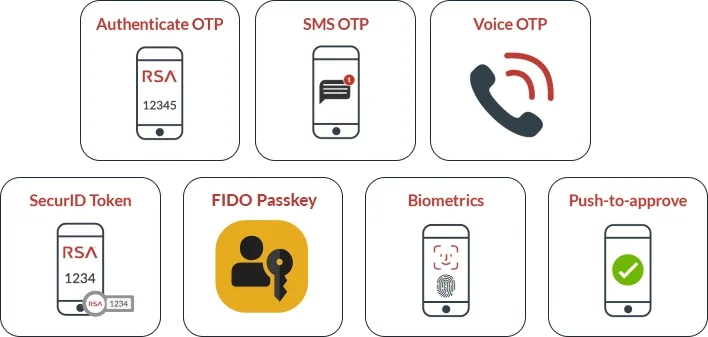
Authentication choices
When the level of access risk warrants another factor of authentication, RSA multi-factor authentication (MFA) provides a range of choices for strong authentication. This keeps an illegitimate attempt from gaining access without placing an unnecessarily high burden on legitimate users.