MFA stands for multi-factor authentication, and as the name suggests, multi-factor authentication (MFA) is the use of multiple factors to confirm the identity of someone who is requesting access to an application, website or other resource. Multi-factor authentication is the difference between, for example, entering a password to gain access and entering a password plus a one-time password (OTP), or a password plus the answer to a security question.
By requiring people to confirm identity in more than one way, multi-factor authentication provides greater assurance that they really are who they claim to be—which reduces the risk of unauthorized access to sensitive data. After all, it’s one thing to enter a stolen password to gain access; it’s quite another to enter a stolen password and then also be required to enter an OTP that was texted to the legitimate user’s smartphone.
Any combination of two or more factors qualifies as multi-factor authentication. The use of only two factors may also be referred to as two-factor authentication.
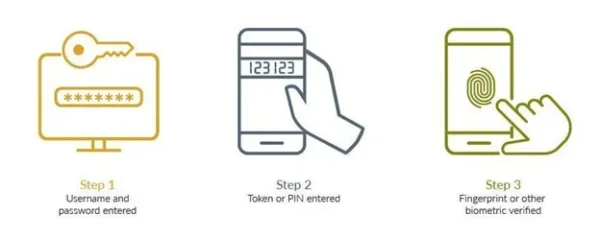
Step One – Username and Password Entered
The first step in the Multi-Factor Authentication process usually involves the user entering their unique username and password. This traditional method of authentication is often the initial line of defense against unauthorized access. Users are prompted to provide their credentials on a secure login page. However, relying solely on a username and password can be inadequate due to various threats, such as phishing attacks, social engineering, adversary-in-the-middle attacks, or third-party data breaches that have made users’ credentials available to threat actors.
Therefore, whether it’s to complete the traditional MFA process or to move beyond passwords, additional verification methods are necessary to enhance an organization’s security posture.
Step Two – Token or PIN Entered
After successfully entering their username and password, most MFA processes ask users to enter a temporary Personal Identification Number (PIN) or one time passcode (OTP). The key characteristic of this step is that the token is time-sensitive and often changes at regular intervals. This means that even if a malicious actor has obtained a user’s password, they would still need access to the token to complete the login process. This dual-verification requirement significantly enhances the security of the user’s account, making it much more challenging for intruders to gain access.
While using OTP as a second factor is far more secure than just using a password, it’s not as secure as other protocols. Moreover, how organizations share OTPs is also an important factor in determining the overall security of the authentication process, with SMS and emails typically regarded as offering lower overall security.
Step Three – Fingerprint or Other Biometric Verified
The final step in the Multi-Factor Authentication process often involves either biometric verification, such as a fingerprint scan, facial recognition, or iris scan, or authentication based on something you have, like a device-bound passkey. Biometrics rely on unique physical characteristics that are extremely difficult to replicate or forge. By requiring a biometric verification in addition to the username, password, and token, MFA ensures that the individual attempting to access the account is indeed the authorized user. This step is particularly valuable in mobile environments, where many devices are equipped with fingerprint or facial recognition technology. Implementing biometric authentication not only enhances security but also provides a seamless and user-friendly experience, as users can quickly and easily verify their identity without needing to remember complex codes.
Device-bound passkeys and other hardware authenticators or hardware tokens also provide enhanced security. Device-bound passkeys are generally hosted on specific ‘security key’ devices, with key pairs generated and stored on a single device. Moreover, the key material itself never leaves that device, making for a more secure authentication flow.
A multi-factor authentication method is typically categorized in one of three ways:
1. Something you know—PIN, password or answer to a security question
Passwords and PINs exemplify knowledge factors. These are secrets known by the user and serve as the first line of defense. As part of MFA, they anchor security in information that is presumed to be memorized by the user and inaccessible to others.
2. Something you have—OTP, token, trusted device, smart card or badge, device-bound passkeys
Ownership of physical devices, such as hardware tokens, device-bound passkeys, or mobile phones, constitutes possession factors. These items frequently hold cryptographic keys or are capable of receiving verification codes, adding an additional barrier for unauthorized access. With possession factors, merely knowing a password is insufficient; access requires something that the user physically holds.
3. Something you are—face, fingerprint, retinal scan or other biometric
Inherence factors relate to an individual’s biometric characteristics. Examples include fingerprints, facial recognition, voice patterns, and even retinal scans. These factors leverage the uniqueness of human biological traits, presenting a substantial hurdle for potential intruders.
Any of the following methods can be used in addition to a password to achieve multi-factor authentication.
- Biometrics—a form of authentication that relies on a device or application recognizing a biometric, such as a person’s fingerprint, facial features or the retina or iris of the eye
- Push to approve—a notification on someone’s device that asks the user to approve a request for access by tapping their device screen
- One-time password (OTP)—an automatically generated set of characters that authenticates a user for one login session or transaction only
- Hardware token or hard tokens or device-bound passkeys—a small, portable OTP-generating device, sometimes referred to as a key fob like the RSA iShield Key 2 series or the RSA DS100 hardware authenticator
- Software token or soft tokens or software authenticators—a token that exists as a software app on a smartphone or other device rather than as a physical token, like RSA’s Authenticator App available on iOS and Android
Improving security
Multi-factor authentication improves security. After all, when there’s just one mechanism guarding a point of access, such as a password, the only thing a bad actor has to do to gain entry is find a way to guess or steal that password. It’s why the majority of data breaches either start with compromised credentials or phishing, which leads to compromised credentials.
But if entry also requires a second (or even a second and a third) factor of authentication, that makes it that much more difficult to get in, especially if the requirement is for something harder to guess or steal, like a biometric feature.
MFA also improves an organization’s Zero Trust maturity and stop phishing with phishing-resistant authentication.
Enabling digital initiatives.
With more organizations eager to deploy a remote workforce today, more consumers opting to shop online instead of in stores, and more organizations moving apps and other resources to the cloud, multi-factor authentication is a powerful enabler. Securing organizational and e-commerce resources is challenging in the digital era, and multi-factor authentication can be invaluable for helping to keep online interactions and transactions secure.
In the process of creating a more secure access environment, it’s possible to create a less convenient one—and that can be a drawback. (This is especially true as zero trust, which treats everything as a potential threat, including the network and any applications or services running on the network, continues to gain traction as a foundation for secure access.) No employee wants to spend extra time every day dealing with multiple obstacles to logging on and accessing resources, and no consumer in a hurry to get some shopping or banking done wants to be waylaid by multiple authentication requirements. The key is to balance security and convenience so that access is secure, but the requirements for access are not so onerous as to create undue inconvenience for those who legitimately need it.
One way to strike a balance between achieving security and ensuring convenience is to step up or dial down authentication requirements based on what’s at stake—i.e., the risk associated with an access request. This is what’s meant by risk-based authentication. The risk can lie with what’s being accessed, who’s requesting access or both.
- Risk posed by what’s being accessed: For example, if someone requests digital access to a bank account, is it to initiate a funds transfer, or just to check the status of a transfer that’s already been initiated? Or if someone interacts with an online shopping website or app, is it to order something, or just to check the delivery status of an existing order? A username and password may suffice for the latter, but multi-factor authentication makes sense when there’s a high-value asset at risk.
- Risk posed by who’s requesting access: When a remote employee or contractor requests access to the corporate network from the same city day after day, using the same laptop every time, there’s little reason to suspect it’s not that person. But what happens when a request from Mary in Minneapolis suddenly comes from Moscow one morning? The potential risk (is it really her?) warrants a request for additional authentication.
Multi-factor authentication is continually evolving to provide access that’s both more secure for organizations and less inconvenient for users. Biometrics is a great example of this idea. It’s both more secure, because it’s tough to steal a fingerprint or face, and more convenient, because the user doesn’t have to remember anything (like a password) or make any other major effort. The following are some of the advances shaping multi-factor authentication today.
- Artificial intelligence (AI) and machine learning (ML)–AI and ML can be used to recognize behaviors that indicate whether a given access request is “normal” and therefore does not require additional authentication (or, conversely, to recognize anomalous behavior that does warrant it).
- Fast Identity Online (FIDO)–FIDO authentication is based on a set of free and open standards from the FIDO Alliance. It enables password logins to be replaced with secure and fast login experiences across websites and apps.
- Passwordless authentication–Rather than using a password as the main method of verifying identity and supplementing it with other non-password methods, passwordless authentication eliminates passwords as a form of authentication.
Be assured that multi-factor authentication will continue to change and improve in the quest for ways people can prove they are who they say they are–reliably and without jumping through hoops.
Try ID Plus cloud multi-factor authentication (MFA) solution—one of the most secure products on the market, and the world’s most deployed MFA. Find out why: sign up for our free 45 day trial.



