Em todo o mundo, os países estão tomando medidas para melhorar a postura de segurança cibernética e se adaptar às ameaças emergentes. As Estados Unidos, União Europeia, Austrália, o Reino Unido, A China e outros países fizeram mudanças significativas em suas regulamentações recentemente.
Como parte de Visão Saudita 2030, Com o objetivo de diversificar a economia do Reino, a Arábia Saudita está adotando medidas semelhantes, lançando a Lei de Proteção de Dados Pessoais em 2023, Controles de Segurança Cibernética de Dados, Controles de Segurança Cibernética de Tecnologia Operacional e um novo kit de ferramentas "para orientar a implementação de controles essenciais de segurança cibernética", de acordo com o Leitura obscura.
Esses compromissos ajudaram o Reino Unido a alcançar a classificação global mais alta no Anuário de Competitividade Mundial do IMD 2024, que avalia o desempenho dos países em estabelecer "as bases para a criação de valor sustentável".
A Autoridade Nacional de Segurança Cibernética (NCA) da Arábia Saudita continua a aproveitar esse progresso, desenvolvendo novas políticas para proteger a infraestrutura de informações críticas do Reino, aprimorar os recursos de segurança cibernética do país e promover um ambiente digital seguro para o governo.
A NCA's Controles essenciais de segurança cibernética (ECC) se aplicam a organizações governamentais no Reino da Arábia Saudita, incluindo ministérios, autoridades, estabelecimentos, empresas, entidades e organizações do setor privado que possuam, operem ou hospedem infraestruturas nacionais críticas (CNI).
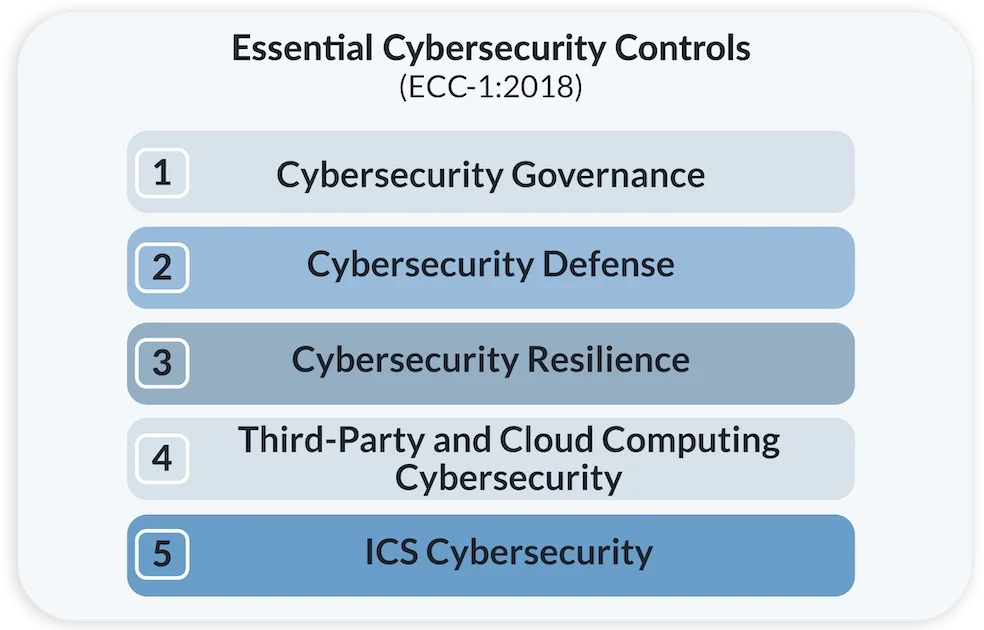
Os controles essenciais de segurança cibernética (ECC) consistem em:
- 5 Principais domínios de segurança cibernética
- 29 Subdomínios de segurança cibernética
- 114 Controles de segurança cibernética
Para as empresas que operam na Arábia Saudita, o ECC é um requisito essencial para manter as operações, proteger os dados e se defender contra ameaças. A falha em cumprir com a regulamentação pode resultar em sanções regulatórias, restrições de participação em contratos governamentais, ações legais, auditorias e um maior risco de ataques cibernéticos.
Com quase duas décadas de experiência trabalhando na Arábia Saudita e ajudando as organizações que priorizam a segurança a cumprir as regulamentações globais de segurança cibernética, a RSA fornece os recursos técnicos de que as organizações precisam para atender às Diretrizes de implementação do EEC e implementar os controles exigidos pelo EEC, inclusive:
- Uma política de senhas para definir a maneira como as senhas são criadas, os requisitos de complexidade, o armazenamento seguro, a transmissão segura, a randomização periódica, o desprovisionamento imediato, o monitoramento contínuo e muito mais.
- Procedimentos de logon seguros para controlar o acesso a sistemas e aplicativos e comprovar a identidade do usuário.
- Padrões que incluem requisitos de controle de acesso específicos da tecnologia.
Dada a ênfase da NCA no IAM, as organizações devem priorizar as soluções que oferecem uma variedade de recursos de autenticação e controle de acesso que priorizam a segurança e atendem a várias exigências de conformidade da NCA.
A RSA Unified Identity Platform fornece os recursos automatizados de inteligência de identidade, gerenciamento de acesso, governança de acesso, autenticação e ciclo de vida de que as organizações precisam para evitar riscos, detectar ameaças e garantir a conformidade:
- Autenticação multifator (MFA): As normas da NCA exigem o uso de MFA forte para verificar as identidades dos usuários antes de conceder acesso a sistemas e dados confidenciais. RSA® ID Plus oferecem uma variedade de opções de MFA, incluindo FIDO, biometria, código QR, autenticadores de hardware (como o novo Série RSA iShield Key 2, com tecnologia Swissbit), push móvel e muito mais.
- Políticas de acesso baseadas em risco de IA: As organizações podem usar RSA® Risk AI para estabelecer políticas de acesso granulares e baseadas em riscos que se alinham às diretrizes da NCA. A solução usa aprendizado de máquina, análise comportamental e contexto comercial para avaliar dinamicamente os perfis de risco do usuário e aplicar controles de acesso adequados em tempo real.
- Governança e administração de identidade (IGA): Governança e ciclo de vida RSA fornece uma plataforma centralizada para integrar, gerenciar e monitorar as identidades dos usuários em toda a organização. A solução permite que as organizações atendam às diretrizes da NCA sobre governança de identidade e controle de acesso.
- Federação de Identidades: O SSO pode simplificar o acesso do usuário em vários aplicativos e remover a autenticação baseada em senha. Minha página da RSA fornece funcionalidade de autoatendimento, gerenciamento de credenciais e experiências de marca que permitem que os funcionários façam login com segurança e acessem vários serviços sem problemas.
Depois de quase duas décadas trabalhando na Arábia Saudita, a RSA se familiarizou com o país, sua cultura e como as novas regulamentações da NCA podem elevar a postura de segurança cibernética das organizações locais. A RSA pode ajudar a sua organização a fortalecer a postura de segurança de identidade, garantir a conformidade com as normas da NCA e proteger os ativos mais valiosos da sua organização, tudo isso enquanto proporciona uma experiência de usuário perfeita para seus funcionários e clientes.
Nossas soluções podem funcionar na nuvem, em ambientes híbridos ou no local - e podem acomodar ambientes adicionais à medida que as organizações adaptam sua infraestrutura a longo prazo. As Programa RSA Ready oferece suporte a integrações com mais de mil soluções de rede de TI, segurança e aplicativos comerciais.
Nossa equipe de especialistas está pronta para trabalhar junto com você para avaliar suas necessidades específicas e implementar nossa solução de forma a otimizar seus esforços de conformidade. Entre em contato conosco para saber mais ou Inicie uma avaliação gratuita de 45 dias do ID Plus hoje mesmo.



