You won’t know where you’re going until you understand where you’ve been. That’s particularly true for identity and access management (IAM): when you look back on the forces that shaped how we authenticate and manage users today some key trends emerge:
- As technology expanded and more users logged on, the number of login ids or “identities” grew exponentially
- As users enrolled in—and started relying on—more interconnected services, they sought out and stuck with accounts that provided frictionless authentication
Last week, I joined Identiverse to review those trends and why they matter more than ever today: more applications and data are moving to the cloud. Remote work is transforming operations. Compliance risks are growing. The perimeter has disappeared. And more users are logging in from more devices than ever.
Identity is at the core of all these trends. And with decentralized identity また、 bot accounts poised to disrupt identity even more, Identiverse came at a moment when many organizations are wondering where they are on their identity journey today—and where they’re headed.
We typically look at IAM as a journey across these four stages:
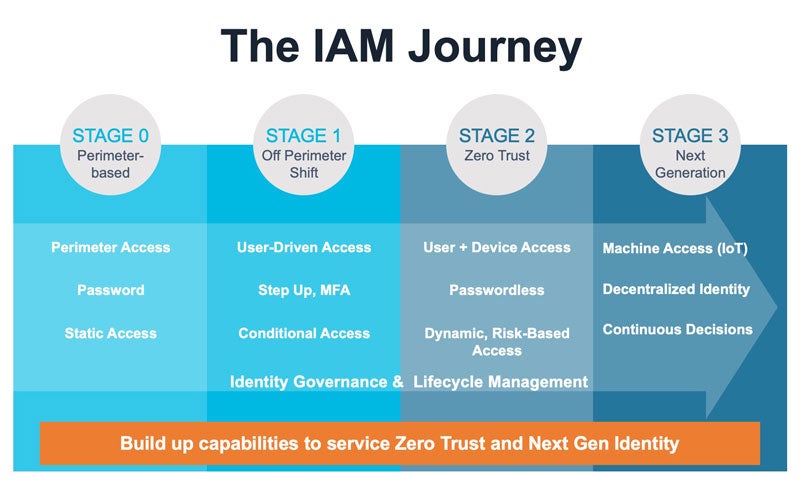
The reality is that many organizations are still early in their journey—managing a network perimeter or a shift to off-perimeter.
Both these stages represent a somewhat outdated method of performing IAM, and you can probably see their limitations: stage 0 and stage 1 IAM tended to work best when users went to an office or specific location to sign into the corporate network. They relied on granting individual passwords that users would have to memorize and manage, typically administered by the IT department. Some organizations have moved up to stage 1, where they use VPN to manage off-perimeter or remote employees.
In too many cases, IAM has been designed around passwords that verify whether a user gets inside the perimeter. Today, that’s a fundamentally outmoded notion for two reasons:
- First, if you’re relying solely on passwords, then you’re building on a vulnerability. The average person has 100 passwords. 80% of hacking-related breaches involved either brute force or the use of lost or stolen credentials. And in addition to being insecure, passwords are also expensive: 50 percent of IT help desk costs are allocated to password resets—that can amount to more than $1 million in staffing just to help your team reset their passwords.
- Second, the perimeter has disappeared—so why are we focused on only protecting it? The coronavirus caused remote work to nearly triple. Instead of a single perimeter network admitting many users in, we now have many perimeters of users and their devices. Every employee has become a branch office of one.
By knowing where they are on the IAM journey today, organizations can plan where they want to go. Those plans should align with a business’ priorities, and in many cases those goals involve some mix of securing company resources; authenticating a wider range of users; controlling total cost of ownership; complying with regulations.
Ultimately, making these investments can provide businesses with a greater ROI on their IAM:
- Deploy multi-factor authentication. Secure operations with multi-factor authentication (MFA). At this point, MFA is a must—it’s such a core security principle that the Biden administration recently released an executive order for public agencies to begin implementing MFA to prevent dangerous and damaging cyberattacks like ransomware. One of the reasons that the Colonial Pipeline ransomware hackers were able to breach the company’s networks is that it wasn’t protected by MFA.
- Go passwordless. In June, the RockYou2021 leak dumped 8.4 billion passwords online—that’s the largest compilation of all time, accounting for almost twice the entire global online population. Passwords are expensive and insecure. Businesses should ditch passwords and go passwordless.
- Enable a hybrid workforce. The one IAM-related advantage of having a hybrid workforce is that a high degree of network traffic can inform smarter authentication decisions: リスクベース認証 helps organizations adapt to the new ‘branch office of one’ dynamic. Smart IAM uses a risk engine and machine learning to baseline every user’s typical behavior and can automate easier or tougher verification requests based on individual access requests.
- Identity governance leads to zero trust. After you authenticate a user, you need to govern what they can do. Setting up role-based access control can help organizations limit what employees, vendors, partners, and customers can do within a network; it also advances ゼロトラスト security strategies that challenge every access request and establish least privilege principles. Smart identity governance and administration (IGA) can also provision new accounts また、 de-provision orphaned accounts automatically, helping to prevent hackers from exploiting legacy credentials. That eliminates a major vulnerability: hackers co-opted an unused VPN account to access Colonial Pipeline.
Getting ahead of these trends is important because the next generation of identity is already in the works.
Decentralized identity will allow users to control who sees their information and what segments of their information they share with certain groups: it will allow me to share different ‘slices’ of my data with my friends, colleagues, or physician.
RSA is working with Solid and the U.K. National Health System on an early use case of decentralized identity, but there are many more in development. Decentralized identity represents a new way for people to use the internet while retaining control of their information.
Likewise, with 127 new IoT devices connecting to the internet every second, we need to start thinking about what bots can do on our behalf.
One thing that’s clear in looking back over the last thirty years is that identity will keep changing—so we’ll need to change with it.



