Una de las mejores cosas de las normas tecnológicas es que ayudan a cualquier solución a hacer aún más.
Por eso hemos buscado la certificación Open ID Connect (OIDC): el nuevo ID Plus Conector certificado OIDC ayuda a las organizaciones a cumplir los marcos normativos, proporciona a los usuarios un mayor control de su información, mejora la experiencia del usuario y desarrolla una seguridad más sólida para los recursos en todos los entornos.
Obtenga más información sobre cómo RSA utiliza su conexión OIDC para cumplir las normas reglamentarias y cómo integramos OIDC con Mi página, La solución de inicio de sesión único (SSO) basada en la nube de RSA, Risk AI, Mobile Lock y mucho más.
OIDC proporciona un estándar de identidad abierto basado en el marco OAuth 2.0 que ayuda a los usuarios a demostrar quiénes son cuando acceden a los recursos de la organización.
RSA ha integrado el protocolo OIDC en nuestras soluciones de gestión de identidades y accesos (IAM), lo que permite a nuestros clientes conectar fácilmente a sus usuarios y proteger sus recursos a través de su solución RSA My Page Single Sign-On (SSO).
En última instancia, la integración de My Page OIDC permite a las organizaciones proteger los recursos OIDC, SAML y locales en un solo portal. Esto facilita a los usuarios el acceso a las aplicaciones que necesitan para realizar su trabajo; también ayuda a los equipos de seguridad a consolidar las aplicaciones y protegerlas de los riesgos.
Pero, ¿qué significa esto en la práctica? Repasemos cómo nuestro conector OIDC ayuda a los clientes de RSA a permitir el cumplimiento, obtener más de RSA Mi página, Tomar decisiones de acceso aún más inteligentes, y mucho más:
Una de las principales ventajas de OIDC es el uso de formularios de consentimiento, que permiten a las organizaciones cumplir con los requisitos normativos que rigen los controles de privacidad de los usuarios, como GDPR, CCPA y otros.
Los formularios de consentimiento permiten a los usuarios comprender y controlar fácilmente la información de identificación personal (IIP) intercambiada entre los proveedores de servicios de identidad y las aplicaciones de terceros basadas en OIDC. OIDC ayuda a los usuarios a comprender qué información de identificación personal se comparte y les ofrece una forma sencilla de evitar que determinada información se transmita desde una solución de identidad a terceros.
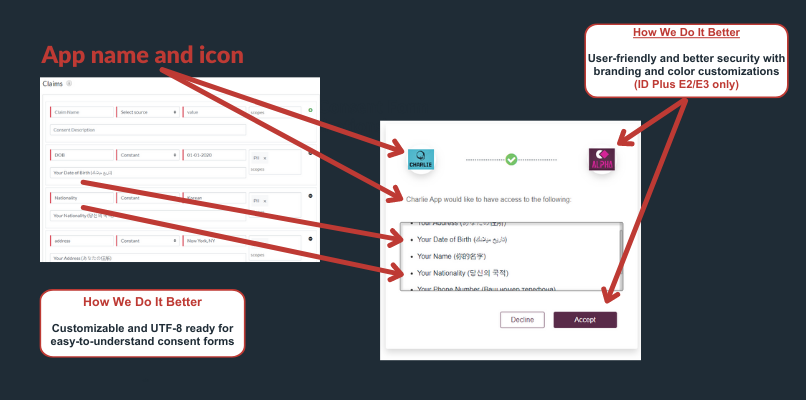
RSA amplía ese beneficio, dando a los administradores y usuarios aún más visibilidad y control sobre cómo se comparte su IIP. El conector OIDC de RSA permite a los administradores personalizar las descripciones de consentimiento de la IIP que podría compartirse entre RSA y aplicaciones de terceros. Por ejemplo, en esta imagen un administrador ha cambiado las descripciones de consentimiento para diferente información (su fecha de nacimiento, su nombre, su nacionalidad, etc.) para que el usuario entienda qué información podría compartirse.
Otros conectores OIDC no ponen el mismo énfasis en la experiencia del usuario: pueden agrupar la IIP como "Contenido e información" sobre el usuario, sus conversaciones, su lugar de trabajo. Los usuarios tendrían que hacer clic en varias opciones diferentes para ver qué tipo de IPI podría compartirse con terceros. Aunque esa experiencia puede cumplir la ley, también es probable que moleste a los usuarios.
Además, las descripciones de consentimiento de RSA OIDC admiten caracteres UTF-8, para que los usuarios puedan leer y comprender el formulario de consentimiento de una organización, independientemente del idioma que hablen.
El formulario de consentimiento también identifica claramente qué aplicaciones están recibiendo IPI mostrando logotipos de terceros. En el ejemplo anterior, el usuario está viendo los datos que se transmiten entre Charlie y Alpha (el logotipo morado). RSA My Page también admite personalizaciones de color y marca, lo que permite a las organizaciones asegurarse de que el estilo del propio formulario de consentimiento esté en consonancia con la marca general.
Mi página es la solución SSO basada en la nube de RSA que ofrece a la fuerza de trabajo híbrida un portal de aplicaciones fácil de usar y personalizable con un portal de autoservicio Authenticator integrado.
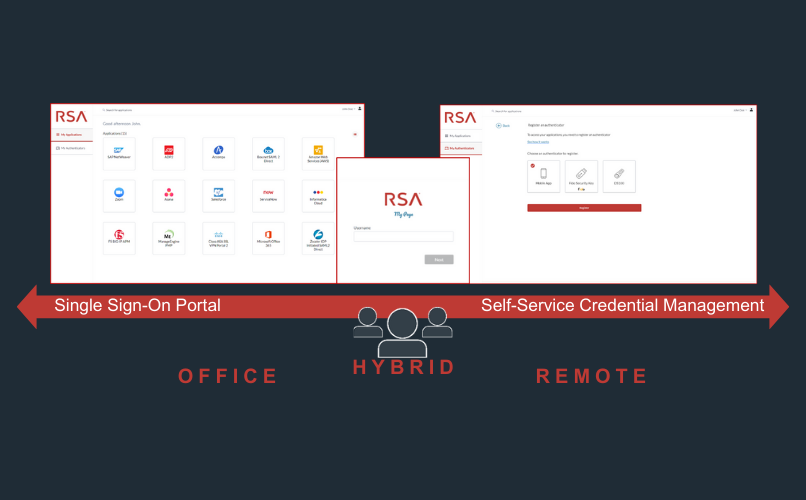
ID Plus es la única solución del mercado capaz de dar soporte a los usuarios en las instalaciones, en la nube y en despliegues híbridos.
Esa ventaja se extiende a la conexión RSA OIDC: la sección "Mis aplicaciones" de Mi Página permite a los usuarios acceder tanto a los recursos OIDC basados en la web y otros recursos web protegidos (SAML) y recursos locales heredados, todo desde el mismo SSO. Los administradores también pueden proteger fácilmente el acceso a estos recursos en distintos entornos configurando políticas de acceso flexibles que permitan a los usuarios seleccionar los métodos de autenticación que mejor se adapten a sus necesidades.
Si los usuarios necesitan restablecer una contraseña, activar un nuevo autenticador, desactivar un autenticador anterior o gestionar de otro modo los autenticadores que utilizan para acceder a los recursos de OIDC a través de "Mis aplicaciones", pueden cambiar a "Mis autenticadores" para realizar el autoservicio.
Esta función es perfecta para quienes pueden gestionar el soporte informático básico por sí mismos, y ayuda a las organizaciones a sufragar los costes del servicio de asistencia. El sitio Informe RSA ID IQ 2023 descubrió que tres cuartas partes de los usuarios desconocían o infravaloraban considerablemente el coste de un restablecimiento de contraseña, por lo que dotar a los usuarios de funciones básicas de asistencia técnica puede suponer un gran ahorro.
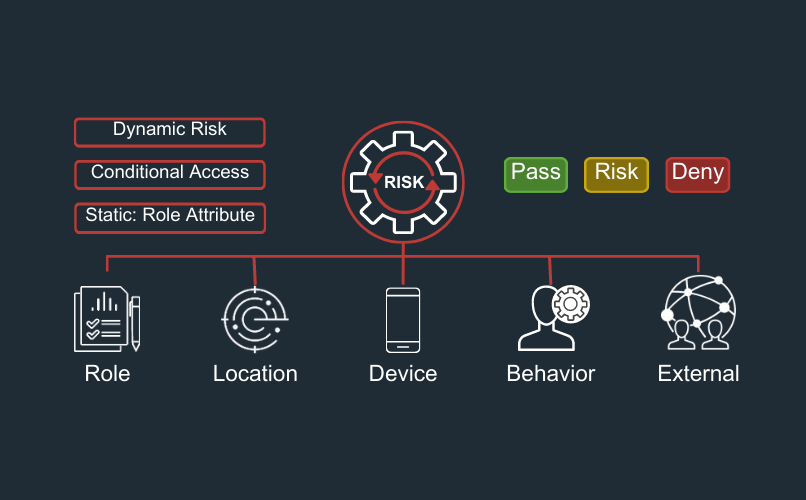
RSA Risk AI utiliza el aprendizaje automático, el análisis del comportamiento y el contexto organizativo para determinar intuitivamente el riesgo de un usuario antes de concederle acceso a sistemas y datos. Utilizamos estos factores para establecer la confianza de la identidad: cuanto mayor es la confianza de la identidad, más probable es que un usuario sea quien dice ser y más probable es que tenga acceso a un recurso protegido.
Por otra parte, una baja confianza en la identidad puede indicar un comportamiento arriesgado. Si un usuario intenta acceder a un recurso desde una nueva dirección IP o un dispositivo no reconocido, eso podría indicar que un atacante ha comprometido una cuenta. El riesgo aumenta si el usuario intenta acceder a un recurso sensible de OIDC.
Los administradores pueden prepararse para estos riesgos, proteger sus activos OIDC de alto valor y desarrollar una ciberseguridad más fuerte estableciendo políticas de acceso de Risk AI para situaciones de baja confianza de identidad. Por ejemplo, los administradores pueden bloquear el acceso directamente o exigir una autenticación escalonada mediante un segundo factor.
Los dispositivos no gestionados y el BYOD son un elemento fijo de la economía del trabajo desde cualquier lugar, pero también suponen un riesgo importante para la identidad: 97% de los expertos en ciberseguridad opinan que el BYOD agrava las principales vulnerabilidades de ciberseguridad, incluido el simple hecho de que los dispositivos no gestionados no tienen las mismas capacidades de seguridad que los dispositivos gestionados, y 72% de los usuarios creen que la gente utiliza con frecuencia dispositivos personales para acceder a recursos profesionales.
Ayudamos a los clientes a adaptarse al aumento de dispositivos no gestionados con Cerradura móvil RSA, que puede establecer la confianza en BYOD y asegurar el acceso a recursos protegidos, incluidas las apps conectadas a OIDC. Cuando Mobile Lock detecta malware u otras amenazas en un dispositivo iOS o Android, les impide utilizar la aplicación RSA Authenticator para acceder a recursos protegidos. Mobile Lock crea un autenticador aún más seguro, lo que a su vez hace que los recursos conectados a OIDC también sean más seguros.

Las organizaciones pueden asegurar mejor el acceso a los recursos de OIDC, mejorar la experiencia del usuario y mejorar la usabilidad con la nueva conexión de OIDC a ID Plus:
- Cumpla la normativa y permita a los usuarios gestionar la información personal con descripciones de formularios de consentimiento que parezcan activos de marca.
- Utilice My Page SSO para que el acceso a los recursos de la organización sea seguro y cómodo.
- Y aplique inteligencia de identidad automatizada con Risk AI y Mobile Lock para desarrollar una ciberseguridad más inteligente y eficaz.



