تتخذ البلدان في جميع أنحاء العالم خطوات لتحسين موقف الأمن السيبراني والتكيف مع التهديدات الناشئة. و الولايات المتحدة الأمريكية, الاتحاد الأوروبي, استراليا, فإن المملكة المتحدة, ، وقد أجرت دول أخرى تغييرات كبيرة على لوائحها مؤخرًا.
كجزء من رؤية السعودية 2030, في إطار برنامج حكومي يهدف إلى تنويع اقتصاد المملكة، تتخذ المملكة العربية السعودية تدابير مماثلة، حيث أصدرت قانون حماية البيانات الشخصية في عام 2023، وضوابط الأمن السيبراني للبيانات، وضوابط الأمن السيبراني للتكنولوجيا التشغيلية، ومجموعة أدوات جديدة "لتوجيه تنفيذ ضوابط الأمن السيبراني الأساسية"، وفقًا القراءة المظلمة.
وقد ساعدت هذه الالتزامات المملكة على تحقيق أعلى تصنيف عالمي في الكتاب السنوي للقدرة التنافسية العالمية 2024 الصادر عن المعهد الدولي للتنمية الإدارية, الذي يقيّم أداء البلدان في إرساء "أسس خلق القيمة المستدامة."
وتواصل الهيئة الوطنية للأمن السيبراني في المملكة العربية السعودية البناء على هذا التقدم من خلال تطوير سياسات جديدة لحماية البنية التحتية المعلوماتية الحيوية في المملكة، وتعزيز قدرات الأمن السيبراني في البلاد، وتعزيز بيئة رقمية آمنة للحكومة.
الهيئة الوطنية للمحاسبين الوطنيين ضوابط الأمن السيبراني الأساسية (ECC) تنطبق على المؤسسات الحكومية في المملكة العربية السعودية، بما في ذلك الوزارات والهيئات والمؤسسات والشركات والكيانات ومؤسسات القطاع الخاص التي تمتلك أو تشغل أو تستضيف البنية التحتية الوطنية الحرجة.
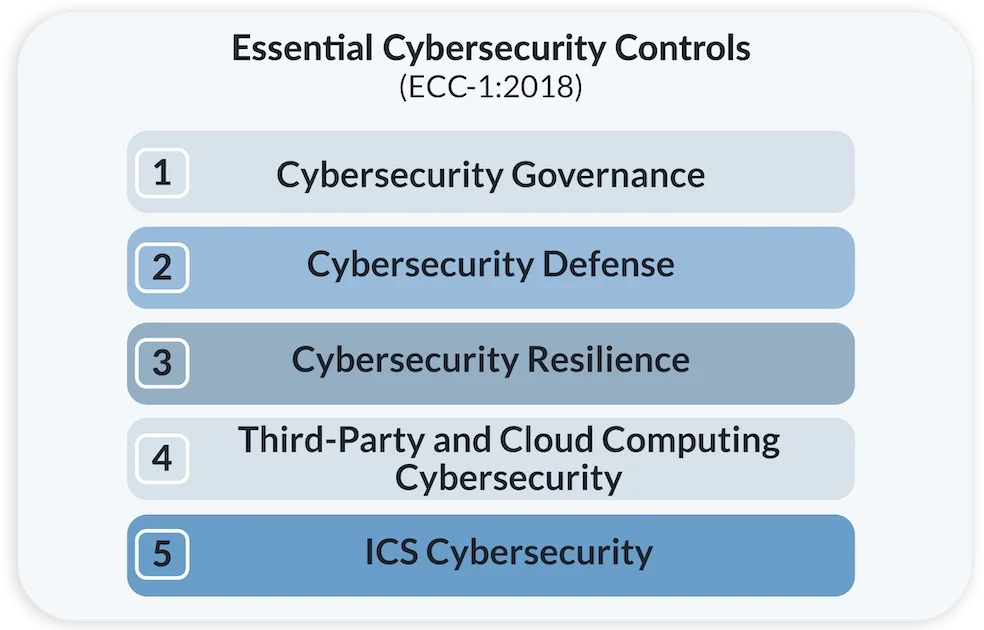
تتكون ضوابط الأمن السيبراني الأساسية (ECC) من:
- 5 مجالات الأمن السيبراني الرئيسية
- 29 مجالاً فرعيًا للأمن السيبراني
- 114 ضوابط الأمن السيبراني
بالنسبة للشركات العاملة في المملكة العربية السعودية، يُعدّ مركز التحكم الإلكتروني مهمة أساسية من مهام الأعمال التجارية وضرورية للحفاظ على العمليات وحماية البيانات والدفاع ضد التهديدات. إن الفشل في الامتثال مع اللوائح التنظيمية يمكن أن يؤدي إلى فرض عقوبات تنظيمية، وقيود على المشاركة في العقود الحكومية، وإجراءات قانونية، وعمليات تدقيق، وزيادة مخاطر الهجمات الإلكترونية.
من خلال ما يقرب من عقدين من الخبرة في العمل في المملكة العربية السعودية ومساعدة المؤسسات التي تضع الأمن في مقدمة أولوياتها، توفر RSA القدرات التقنية التي تحتاجها المؤسسات لتلبية إرشادات التنفيذ الخاصة بالجماعة الاقتصادية الأوروبية ونشر الضوابط التي تتطلبها الجماعة الاقتصادية الأوروبية، بما في ذلك:
- سياسة لكلمات المرور لتحديد طريقة إنشاء كلمات المرور، ومتطلبات التعقيد، والتخزين الآمن، والنقل الآمن، والعشوائية الدورية، والإلغاء الفوري لكلمات المرور، والمراقبة المستمرة، وغير ذلك.
- إجراءات تسجيل الدخول الآمنة للتحكم في الوصول إلى الأنظمة والتطبيقات وإثبات هوية المستخدم.
- المعايير التي تتضمن متطلبات التحكم في الوصول الخاصة بالتكنولوجيا.
ونظراً لتركيز NCA على إدارة الوصول إلى المعلومات والاتصالات، يجب على المؤسسات إعطاء الأولوية للحلول التي توفر مجموعة من إمكانيات التحكم في الوصول والمصادقة التي تعالج العديد من تفويضات الامتثال لـ NCA.
توفر منصة RSA Unified Identity Platform (منصة الهوية الموحدة) قدرات ذكاء الهوية الآلي وإدارة الوصول وحوكمة الوصول والمصادقة ودورة الحياة التي تحتاجها المؤسسات لمنع المخاطر واكتشاف التهديدات وضمان الامتثال:
- المصادقة متعددة العوامل (MFA): تشترط لوائح الهيئة الوطنية للمحاسبين الوطنيين استخدام المصادقة الآلية القوية للتحقق من هويات المستخدمين قبل منحهم حق الوصول إلى الأنظمة والبيانات الحساسة. RSA® ID Plus توفر مجموعة من خيارات المصادقة الآلية، بما في ذلك FIDO، والقياسات الحيوية، ورمز الاستجابة السريعة، وأجهزة المصادقة (مثل RSA iShield Key 2 Series, المدعوم من Swissbit)، والدفع عبر الهاتف المحمول، وغير ذلك الكثير.
- سياسات الوصول المستندة إلى المخاطر المستندة إلى الذكاء الاصطناعي: يمكن للمنظمات استخدام RSA® Risk AI لإنشاء سياسات وصول دقيقة وقائمة على المخاطر تتوافق مع إرشادات NCA. يستخدم الحل التعلّم الآلي والتحليلات السلوكية وسياق الأعمال لتقييم ملفات تعريف مخاطر المستخدم بشكل ديناميكي وفرض ضوابط الوصول المناسبة في الوقت الفعلي.
- حوكمة وإدارة الهوية (IGA): حوكمة ودورة حياة RSA® منصة مركزية لإعداد هويات المستخدمين وإدارتها ومراقبتها عبر مؤسستك. يُمكِّن الحل المؤسسات من تلبية توجيهات الهيئة الوطنية للمحاسبين الوطنيين بشأن حوكمة الهوية والتحكم في الوصول.
- هوية موحدة: يمكن لـ SSO تبسيط وصول المستخدم عبر مختلف التطبيقات وإزالة المصادقة المستندة إلى كلمة المرور. RSA صفحتي يوفر وظائف الخدمة الذاتية، وإدارة بيانات الاعتماد، والتجارب ذات العلامات التجارية التي تسمح للموظفين بتسجيل الدخول الآمن والوصول بسلاسة إلى خدمات متعددة.
بعد ما يقرب من عقدين من العمل في المملكة العربية السعودية، أصبحت RSA على دراية بالبلد وثقافتها وكيف يمكن للوائح الجديدة للهيئة الوطنية لمكافحة الجرائم المعلوماتية أن ترفع من موقف الأمن السيبراني للمؤسسات المحلية. يمكن أن تساعد RSA مؤسستك في تعزيز وضع أمن الهوية لديك، وضمان الامتثال للوائح الهيئة الوطنية لمكافحة الفساد، وحماية الأصول الأكثر قيمة لمؤسستك، كل ذلك مع تقديم تجربة مستخدم سلسة لموظفيك وعملائك.
يمكن أن تعمل حلولنا في السحابة، أو عبر البيئات المختلطة، أو في أماكن العمل - ويمكنها استيعاب بيئات إضافية مع قيام المؤسسات بتكييف بنيتها التحتية على المدى الطويل. إن برنامج RSA Ready يدعم التكامل مع أكثر من ألف حل من حلول شبكات تكنولوجيا المعلومات والأمن وتطبيقات الأعمال.
إن فريق الخبراء لدينا على استعداد للعمل معك عن كثب لتقييم احتياجاتك الخاصة وتنفيذ حلنا بطريقة تحسن من جهودك في مجال الامتثال. اتصل بنا لمعرفة المزيد أو ابدأ تجربة 45 يوماً على ID Plus مجاناً اليوم.



